by KeeeX | Nov 23, 2016 | News, Press Release, Tech Zone
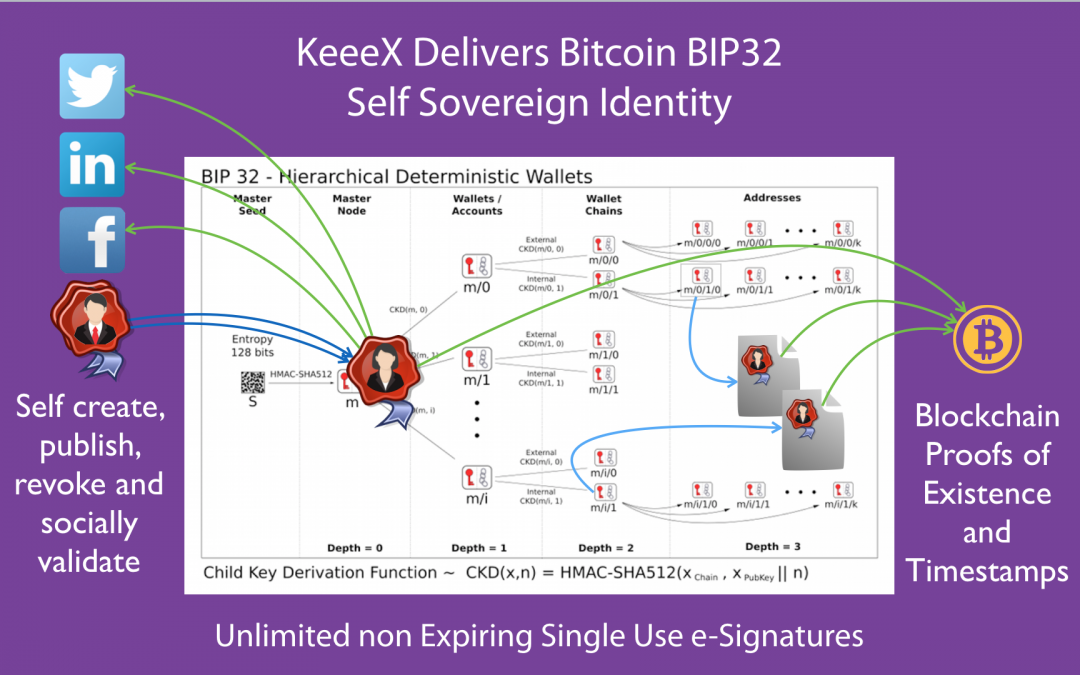
For the first time ever, BIP32 hierarchical deterministic wallets can be used to self define, publish, and revoke a cryptographic identity. This identity can be used to generate one time signatures for every item signed, hence achieving unprecedented signature security.
How it works
The identity is defined as the public master key of any node in a bip32 tree. This pub key can be shared, published at will, for instance on social networks.
Every signature can be traced to the corresponding public master key without ever exposing the corresponding private master key.
A demo
To test, you may download our demo file, then verify it on https://verify.keeex.io, and hopefully search the web for the master identity used: xpub6BBj7rHc3YY3v3Xxj4B7UHSuM6bQJSPugj3BRY7yaHEZg8HDSEkoBfWJqbbXCB9ECjcJp3vV1CzrPmMdeLCGRLRTsvu5suE5UbbrYHg9D4p
You can play with BIP32 here.
Further reading
And view the BIP32 specifications there.
by KeeeX | Nov 10, 2016 | Press Release, Tech Zone

by KeeeX | May 10, 2016 | News, Tech Zone
We are publishing a bug bounty challenge to crack our encrypted container, thanks to BugBountyZone.com.
We are extremely proud to accompany the launch of their new bug bounty platform.
Note that KeeeX offers ultimate confidentiality by encrypting using totally anonymized containers (that neither disclose any hint of who are the sender and receivers nor of what is the data), that may further be exchanged using your own cloud or disk.

by KeeeX | Feb 4, 2016 | News, Press Release, Tech Zone
As of version 2.3.0 released end of January 2016, the amazing value of KeeeX if now further protected with universal 2 factor FIDO (the FIDO standard is promoted by the Fido Alliance). This means that you can use any FIDO device (as e.g. Neowave’s Keydo, Yubico’s key…) to protect your KeeeX account.
Further protecting your KeeeX account means protecting an amazing range of your unique serverless collaboration : messaging, chats, ECM (document and content management, versions, classification…), processes, search, integrity.

by KeeeX | Jan 27, 2016 | News, Tech Zone, What KeeeX is For, White Paper
Two innovations that illustrate applications of immutable and connected data tend to widely disseminate in our lives. Can we complement or improve on this and what do we learn?
One is Git. Git is the most widely used version control system. The emphasis of Git on data integrity builds upon an underlying scheme called “content addressable storage” and Merkle trees.
(more…)
by KeeeX | Sep 24, 2015 | Slideshow, Tech Zone
Slides presented at Connect Security World Marseille 2015 (xonom)
KeeeX lets users define per recipient sharing means (over weblinks, dropbox, google drive, even nfs or webdav) and encryption settings.
Then sharing targets can be selected in a single click: no groups, no access rights, extreme simplicity.
KeeeX is a unique no infrastructure, #nosaas solution.
by KeeeX | Sep 24, 2015 | Slideshow, Tech Zone
These slides were presented at the World e-Id and Cybersecurity conference in Marseille (xuheg)
KeeeX lets users define their own identity settings using a social certificates: people who know you ensure that you are the one you pretend, in the absence of a certificate authority.
Social certificates can be renewed, published, revoked at any time, at no cost.
KeeeX won an award at World Smart Week in the category e-Id and Cybersecurity.
KeeeX is a unique no infrastructure, #nosaas solution.

by KeeeX | Jun 23, 2015 | Tech Zone, White Paper
KeeeX is a true solution devoid of trusted tiers, and is not the next ‘Bad Guy’. You have access to everything, even in the future should the KeeeX company default. And KeeeX does not see a byte of your Data. (more…)
by KeeeX | Jan 27, 2015 | News, Tech Zone
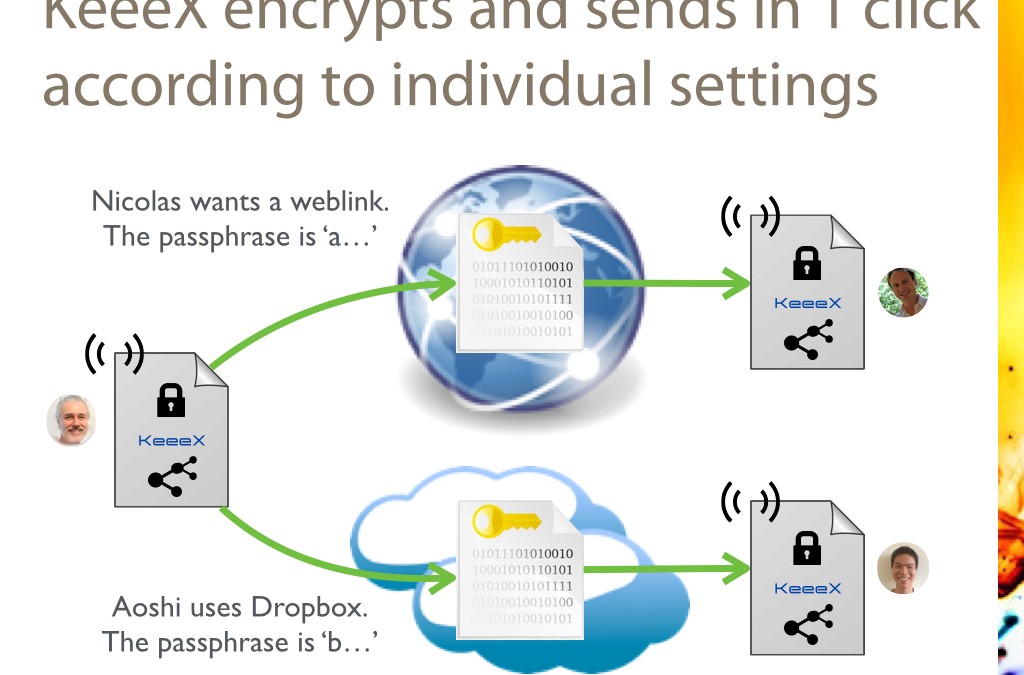
KeeeX beta Lydig 1.7 is online! Now, your files and documents are by default automatically sent via weblinks via a partnership with Jaguar Network, or can be copied to your favorite cloud sync or shared folders.
And they are instantly received, and automatically moved next to their previous version if any.
They are also ultimately protected from prying eyes by automatic client side AES 256 encryption, and automatic receiver side decryption. No stress, no risk in the confidentiality of your industrial of intellectual property.
You pick a shared secret with a collaborator. KeeeX recalls it, as long as you need.







