by KeeeX | May 25, 2016 | They talk about us
“… Hence the most positive viewpoint that we can have on this technology is naturally ethical. The blockchain is a facilitator and a source of savings. It also provides the foundation of pacified relationships, in the economy, industry, relation with authorities and the respect of individual rights. …”
http://www.lesechos.fr/idees-debats/cercle/cercle-157119-la-blockchain-de-la-monnaie-virtuelle-a-lethique-1223076.php
by KeeeX | May 24, 2016 | HowTo, Help, News
This slideshow provides highh level insights of the features and properties of KeeeX Messenger.
The Ultra Secure, Rich, Probative Enterprise Messenger
No Infrastrucure, Data remains under absolute user control
Leak free, Cheat free, Loss free, Tie-in free, Blockchain trust
Reclaim and Futurize your Collaboration – May 2016

by KeeeX | May 23, 2016 | News, Non classé, What KeeeX is For
KeeeX records at will proofs of existence of any of your files on the Bitcoin blockchain. On course, one may use this for very serious things : contracts, certified diplomas, minibonds, proofs of ownership or insurance claims…
But we may use this to immortalize our selfies forever! Specially with the latest KeeeX for Android beta, that is readily available. One full month free testing under the current terms.
For photographers and authors KeeeX also allows for injecting your copyright settings straight inside the document you’re publishing.
(Photo credit David Blackwell – Creative Commons Attribution-NoDerivs 2.0 Generic – https://www.flickr.com/photos/mobilestreetlife/12255093704/in/photostream/ – Thanks)
by KeeeX | May 13, 2016 | They talk about us
https://www.frenchweb.fr/3-start-up-francaises-qui-innovent-avec-la-blockchain/239443#c3xOQ5YVAPQPQeIw.99
Thanks

by KeeeX | May 10, 2016 | News, Tech Zone
We are publishing a bug bounty challenge to crack our encrypted container, thanks to BugBountyZone.com.
We are extremely proud to accompany the launch of their new bug bounty platform.
Note that KeeeX offers ultimate confidentiality by encrypting using totally anonymized containers (that neither disclose any hint of who are the sender and receivers nor of what is the data), that may further be exchanged using your own cloud or disk.

by KeeeX | May 3, 2016 | News, Press Release
We are proud to announce that EMD Management has chosen KeeeX to provide certified smart diplomas to their students. Such smart diplomas can be verified as genuine at any point in the future by anyone, by just matching the Bitcoin blockchain ledger with the verified document and timestamp certificate. This operation simply amounts to dropping them on the free version of KeeeX.
The deal was concluded by Xavier Palou (EMD Director) and Laurent Henocque (KeeeX founder), by mutually digitally signing and blockchain timestamping a digital agreement, created in the form of a simple KeeeX discussion. The timestamp certificate can be found here, then downloaded and verified.
The EMD Alumni will now receive their smart diplomas, generated via KeeeX by one click operations. All participants remain in absolute control of the certified documents and proofs. The whole scheme is fully operational in the current KeeeX Tigon.
EMD will be relieved from responding to diploma validity inquiries.
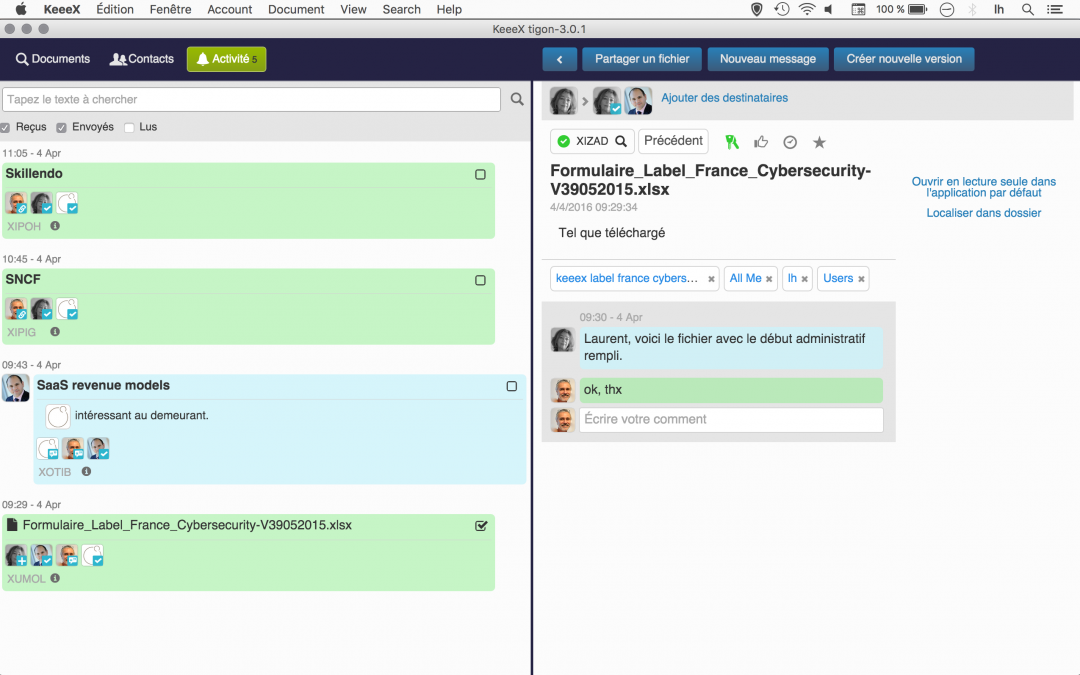
by KeeeX | Apr 5, 2016 | News, Press Release
We’re extremely proud and happy to have you on our side and welcome you on this blog.
The KeeeX team has been hard at work to release what we believe is among the most beautiful collaboration tools ever. It combines the power of a rich and agile professional instant messenger, fully private file sharing, versioning, chaining, tagging, commenting, approving, signing, timestamping, integrity…
The new KeeeX v3.0 is called ‘Tigon’, from the name of a delicate heart shaped flower, or sometimes of an hybrid of a lion and a tiger. It provides unprecedented ease of use, to initiate an instant chat, securely share a file, create a new version, manage a task list… All this without revealing a single byte of your data, in a decentralized way, beyond enterprise limits, without complex group or access rights, version name, date and password management. Away from email.
KeeeX Tigon also provides one clic timestamping over the Bitcoin blockchain of any contract, document, photograph, invention, creation, proof, copyright… You will create your own uses, or simply will love the fun of registering a selfie forever.
We also wish to inform you ahead of time that the current ‘Collaboration Launch’ plan allows for unlimited timestamping. Leak, cheat and tie-in free. Enjoy!
Laurent and the KeeeX team

by KeeeX | Feb 4, 2016 | News, Press Release, Tech Zone
As of version 2.3.0 released end of January 2016, the amazing value of KeeeX if now further protected with universal 2 factor FIDO (the FIDO standard is promoted by the Fido Alliance). This means that you can use any FIDO device (as e.g. Neowave’s Keydo, Yubico’s key…) to protect your KeeeX account.
Further protecting your KeeeX account means protecting an amazing range of your unique serverless collaboration : messaging, chats, ECM (document and content management, versions, classification…), processes, search, integrity.
by KeeeX | Feb 1, 2016 | What KeeeX is For, White Paper
KeeeX addresses a large number of Records Management (Wikipedia) issues as stated in this Wikipedia definition page. Let’s review some of them:
Concerning Digital Records
…It is more difficult to ensure that the content, context and structure of records is preserved and protected when the records do not have a physical existence. This has important implications for the authenticity, reliability, and trustworthiness of records…
KeeeX proves integrity, authenticity, authorship of virtually any digital content.
Particular concerns exist about the ability to access [and read] electronic records over time
KeeeX identifiers are indexed by search engines, hence allowing for unprecedented accessibility and robustness to renaming and moving.
Privacy, data protection, and identity theft have become issues of increasing interest.
KeeeX leaves files where originals are. No transfer is made for processing. When files need to be transferred, they are encrypted end to end. KeeeX implements digital signatures that prevent for identity theft as well.
The increased importance of transparency and accountability in public administration, marked by the widespread adoption of Freedom of Information laws, has led to a focus on the need to manage records so that they can be easily accessed by the public.
KeeeX allows for publishing documents that can be accessed by search engines, and hence made freely available to the public, who can verify their integrity for free. Check for instance this search: https://duckduckgo.com/?q=”xofos-bafek-zebug”.
Implementing required changes to organizational culture is a major challenge, since records management is often seen as an unnecessary or low priority administrative task that can be performed at the lowest levels within an organization.
Using KeeeX, documents are classified and protected as part of everyday work and do not require extraneous actions.
A difficult challenge for many enterprises is tied to the tracking of records through their entire information life cycle so that it’s clear, at all times, where a record exists or if it still exists at all.
KeeeX will help track all successive versions of a record. Each specific version can be meta searched anywhere, including on a company’s disks, to assess whether the file still exists or not.
The tracking of records through their life cycles allows records management staff to understand when and how to apply records related rules, such as rules for legal hold or destruction.
Specific rules can be attached to records either informally in embedded descriptions of more formally using classifiers. It becomes possible, even in the absence of any tool, to track on company’s disks and servers all record instances that should be legally present or that should legally have been deleted.
Concerning Physical Records
Records must be stored in such a way that they are accessible…
When a physical record has been scanned, it may naturally receive the KeeeX identifier of this scan, that can be used for storing and retrieving. This is so because these identifiers are humanized, and hence can be subject to alphabetical sorting. Such an archival strategy is considerably more robust to mis-classification than hierarchical folder archival.
(this complements a document previously published on Slideshare and this blog. As a proof that KeeeX provides unprecedented records management possibilities, you may try this web search: https://duckduckgo.com/?q=xofos-bafek-zebug)

by KeeeX | Jan 30, 2016 | White Paper
Thursday January the 28th was #DataPrivacyDay (or #DataProtectionDay).
CEO, CTO, CIO, CFO, did you take any action?
Do you really still use email ???
Stop leaking your IP on email, untrusted clouds and collaboration solutions.
Stop leaking your IP with co-workers taking work at home using an untrusted synchronization system.
What will happen when you wish to file a patent and some obscure company has beaten you in the race with obvious cheating?
Start using KeeeX, the only durable, risk free, investment free, no-tie in, #nocloud, #nosaas, trusted zero knowledge message+content+process management solution that lets your colleagues send work anywhere, home inclusive, at no risk.

by KeeeX | Jan 27, 2016 | News, Tech Zone, What KeeeX is For, White Paper
Two innovations that illustrate applications of immutable and connected data tend to widely disseminate in our lives. Can we complement or improve on this and what do we learn?
One is Git. Git is the most widely used version control system. The emphasis of Git on data integrity builds upon an underlying scheme called “content addressable storage” and Merkle trees.
(more…)

by KeeeX | Jan 23, 2016 | News
Our brand new KeeeX now supports FIDO Universal 2 factor authentication. This means that your account is fully protected by the USB key in your pocket, and this covers the incredible sum of KeeeX features:
- fully private messaging
- amazing serverless file versioning, semantic organization and sharing (files stay yours)
- incredibly fast search – never lose a file any more
- 1-1 direct file transfer and encryption settings
- ultra flexible process management (from simple “todo” to full fledged scrum or crm processes)
- unique digital signatures with zero certificates
- … and so much more to discover and to come
Come discover then enjoy the unique zero knowledge app that will help you detox your work.

by KeeeX | Jan 2, 2016 | News
The KeeeX team is happy to present you their best wishes for the new year 2016.
Of course we imagine that with a little help from KeeeX, you’ll experience collaboration to the highest quality standards.
With warm regards,
Ngu “Aoshi”, Françoise, Clément, Maxence and Laurent
by KeeeX | Dec 23, 2015 | News
During 92 days, from the solstice on december 2015 the 22th to the equinox on march 2016 the 22th, earn two free ‘Collaboration’ license months for every new and active user that you invited to KeeeX by sending an email from within the app.

by KeeeX | Dec 23, 2015 | News, Slideshow

by KeeeX | Nov 23, 2015 | White Paper
The current trend in mobile device use at work leads to install ever increasing numbers of apps, for multiple uses, from Business Intelligence to Messaging. Some corporate tools are connected to centralized information sources and hence do not result in duplicated data silos. Other don’t.
When apps help users produce valuable data, it is a problem when this data cannot be seamlessly exploited by other, maybe future unknown processes. Disconnected data silos yield disconnected processes. Disconnected processes increase total cost of ownership far beyond the expected initial price tags.
The reason why apps create isolated data silos is because they are not designed to share the data they create. Most often the data is uploaded to the cloud for exploitation, or sometimes stored in a local database. More specifically, SaaS web apps just cannot by design freely access the local drive for obvious security reasons. So data must go to the cloud or a local database. Of course, syncing, collaboration applications must use data cloud stores to present the data to multiple parties.
So the situation is as follows: we need (collaboration) apps for productivity, but using the new trendy (and probably best) app will add one brick to future disconnected processes.
One solution to this problem is to reverse the perspective: instead of placing data inside trusted organizing silos, place trust and organization inside data, so that data can live in the open, outside of any silo, available for unlimited processes, unlimited future exploitation. This is what we are doing at KeeeX.

by KeeeX | Nov 13, 2015 | News
Final pitch will take place on November the 19th in Trento, Italy.
The totally unique approach to PI protection by KeeeX is once more recognized.
by KeeeX | Oct 19, 2015 | Pitch, Slideshow
by KeeeX | Oct 9, 2015 | What KeeeX is For, White Paper
At KeeeX, we are leveraging a patented innovation allowing to augment virtually any file with integrity/authenticity/linking cleartext searchable metadata that opens new perspectives for Open Access (and more generally Open Data).
- file integrity and authorship are builtin.
- references to other papers and documents, semantic classification and context are builtin.
- wherever a file is found, it can be verified as genuine using our simple client or a web site.
This means that:
- Open Research can be published *anywhere*: including a publicly available cloud folder.
- Open Access documents can be retrieved using general purpose search engines.
- any document that refers to another document, if keeexed, will allow to embed the exact identifier to its references, that can themselves be searched then verified locally as genuine.
Of course we provide a paid solution for businesses, but also we develop an academic program, and in any case producing some amount of publishable documents will be possible using the free version.
I’d be extremely happy to help anyone reading this to test KeeeX, for instance in the purpose of studying its potential in Open Access.
If you’re an academic and are willing to use KeeeX in your institute, please feel free to contact us.
This post was created as a comment to a discussion about the future of Open Access publishing.

by KeeeX | Oct 6, 2015 | News, White Paper
Do you believe too that bringing the productivity and agility benefits of social collaboration to the enterprise must necessarily imply using SAAS applications? (more…)













